If you have data living in the cloud (who doesn’t nowadays?) and an ecommerce business, you should be taking cybersecurity seriously. October is cybersecurity month, but doing everything you can to ensure your data is secure is a year-round endeavor.
A number of cloud services are readily available for businesses to improve their day-to-day operations, including Amazon Web Services (AWS), Google Cloud Platform (GCP), and other Infrastructure-as-a-Service (IaaS) providers. These services have allowed organizations to expand and grow their business. But while AWS and GCP excel in helping enterprises deploy Software-as-a-Service (SaaS) products, they may not offer sufficient protection for data stored in the cloud.
There is a naive level of trust in cloud computing that has permeated our daily lives. [The] illusion that the cloud is a magical place where your data is easily recoverable and available on all your devices, regardless of what apps you use.
– James Ciesielski, CTO & Co-Founder, Rewind
The 2020 pandemic forced many brick and mortar companies to move much of their business online – e.g., allowing employees to work from home, signing up for new SaaS services, introducing new ecommerce stores, or expanding their existing ones. While this sudden change helped protect employee safety, maintain business continuity, and recover some of the revenue lost to decreased foot traffic, the rapid shift to doing business online also introduced multiple security and data protection issues.
This article discusses the importance of implementing cybersecurity measures, the limitations of cloud computing, and tips on how to apply cloud security protocols.So, let’s start with the basics.
What is cloud security?
So, what is cloud security? And how secure is the cloud? Cloud security is a collection of technologies, services, controls, and practices designed to protect cloud data, applications, and infrastructure from cyber threats and attacks. Robust cloud cyber security is essential to prevent data loss and help the organization maintain compliance with data privacy regulations.
Cloud cyber security can be supplied by the cloud service provider (CSP) or the customer. In most cases, the CSP offers their customers the latest in cloud cyber security technology and ensures they have the best possible protection from known and anticipated threats.
Why is cloud security important?
Cyber security becomes a critical concern as more companies complete their digital transformation and migrate systems to the cloud. As the threat environment is constantly evolving, it is vital to reduce the risk of cloud computing as much as possible and ensure data and systems are protected at rest, in use, and in transit.
If cloud data is compromised, companies risk loss on several levels. Loss of revenue, reputation, and business continuity are at issue. The average cost of a data breach is in the realm of $8.64 million, and it typically takes 280 days for a company to detect, remediate, and recover. Additionally, many companies won’t survive a significant breach, making an irrefutable argument in favor of cloud cyber security.
Data is growing exponentially, and cloud providers are dealing with greater risks of data breaches. As the data grows, so does the attack surface. Data security is the fundamental right of human beings, and with data migrating to a cloud environment, a cloud security solution is more of a necessity than a want.
Cloud computing security risks are rising, and cloud providers are working towards securing the cloud environment with various safeguards such as encryption to ensure that cloud data is secure from both accidental deletion and malicious attacks.
Now, let’s take a deeper dive to answer the question, what is cloud computing, and how does cloud computing work?
What is cloud computing?
Cloud computing is a method of delivering computing services over the internet, including servers, storage, networks, software, and analytic data. Companies choose cloud computing to reduce costs, gain agility, and improve cloud security. As cloud services, including cloud security, are easily scalable, it is a way to support continuity even during times of rapid growth.
Cloud computing services
Cloud services can appear in one of three ways depending on the service an organization offers to its customer. These three are SaaS, PaaS, and IaaS. Let see what each of these mean.
Software as a Service (SaaS) is a cloud application service. Organizations frequently use this to deliver their applications to the end-user, while a third party manages the application through a private cloud.
Platform as a Service (PaaS) is a cloud platform service that allows developers to work on their applications through the cloud. This simplifies their development management process and allows them to solely focus on development while the organization or a third party manages the server, storage, and networking.
Infrastructure as a Service (IaaS) offers organizations a complete working infrastructure, from storage, networking, monitoring, and other services, all on a private cloud. This simplifies the management practices of an organization and frees resources that would have otherwise been used in the case of legacy infrastructure.
Risk of cloud computing
The benefits of using an IaaS provider are obvious. There is no need to spend money on buying and maintaining expensive servers and computing power, along with a general sense that your data is safe because it’s “in the cloud.” However, business owners would be wise to check the fine print around how protected that data really is.
When you host your data in the cloud, the IaaS provider is responsible for the protection of the foundational infrastructure, whereas business owners are responsible for protecting their own data. The primary risks you’ll face include:
- Data privacy compliance
- Data breaches
- Unauthorized access
- Malware infections
- Cyberattacks
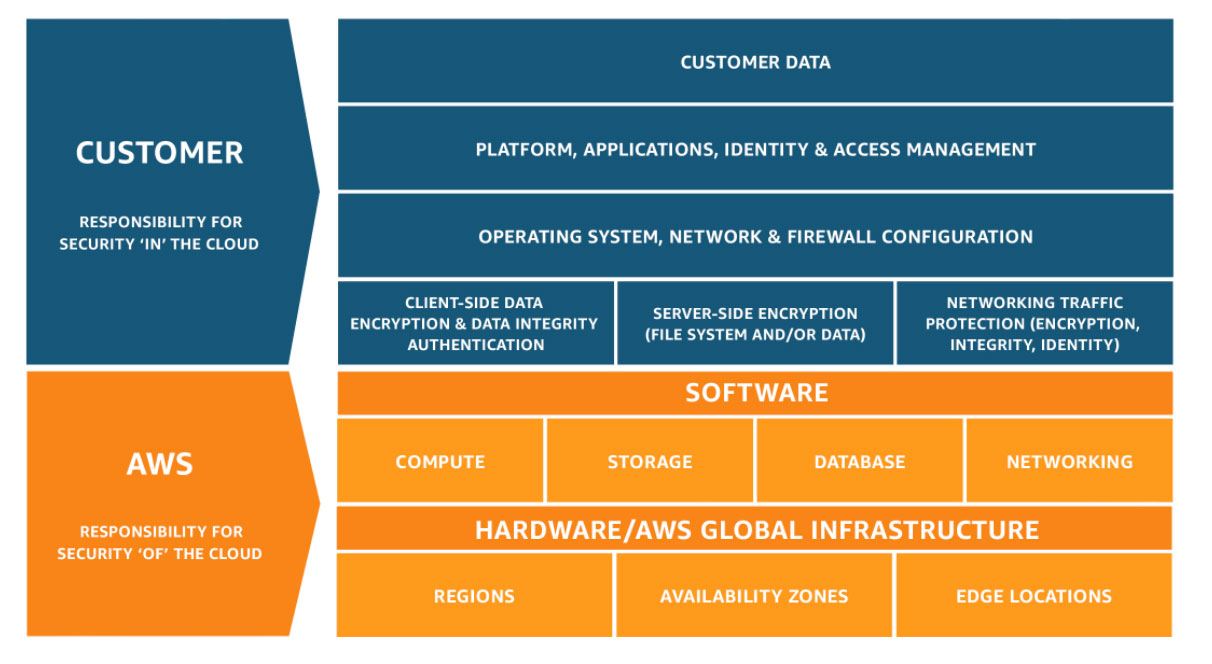 Source: Awsstatic
Source: Awsstatic
This model clearly portrays how the customers and cloud services communicate with each other. The IaaS provider supports you by giving you secure infrastructure, bandwidth access, and disaster recovery, but it is up to you to be aware of the limitations of cloud computing and how you protect your information.
Learn more about how the Shared Responsibility Model affects businesses using SaaS apps.
Top cloud security threats
There are several threats associated with the cloud, and some of these are not typically taken into consideration. Below, we’ll discuss the top five security threats your organization is exposed to when on the cloud.
Misconfigured cloud services
One of the major problems that organizations face is cloud misconfigurations. Even though they’re easily preventable, the major cause of this threat is mere human negligence. Misconfiguring your cloud service can open the path to unauthorized access to your server. This can lead to greater problems moving forward.
Data loss
When you’re using a platform that makes data transfer so simple, it’s no surprise that you’re opening the door to data loss. Several organizations have said that data loss and sprawl are their biggest issues with cloud storage. When you migrate large amounts of data to the cloud, there will always be a chance of data loss. The best answer to this is to create updated backups for all your data stores.
API vulnerabilities
Cloud services rely heavily on APIs to communicate with applications. It might seem like a neat little tool, but these APIs are the most prone to cyberattacks. Hackers can launch DoS attacks and inject codes to break into the cloud server and access the organization’s personal data.
Malware attacks
Since the cloud is easily accessible, it becomes accessible to people with ill-intent. To top it off, cloud environments are connected, which means if there is an attack, the damage spreads like wildfire. Some of the most dangerous instances of cyberattacks can include hyperjacking, DoS attacks, and hypervisor infections.
Insufficient access management controls
When you place all your data in one place but don’t want everyone to see it, problems can occur. Cloud storage is a cheaper way to store all your data and free up resources within your organization, but most organizations forget that not all data is for everyone. Hasty cloud migration can put all your data out in the open for anyone to access.
Before migrating the data, be sure to have appropriate access controls in place. Insufficient safeguards identity policies not only increase the risk of external attacks but also increase the chances of human error and employee negligence.
Cybercrime & cloud computing
In recent years, big companies like Adobe, Sony, Target, Equifax, and Marriott have suffered from cyberattacks. The annual Accenture’s report, Cost of Cyber Crime, has identified more than half a dozen techniques being used by criminals to compromise or delete data:
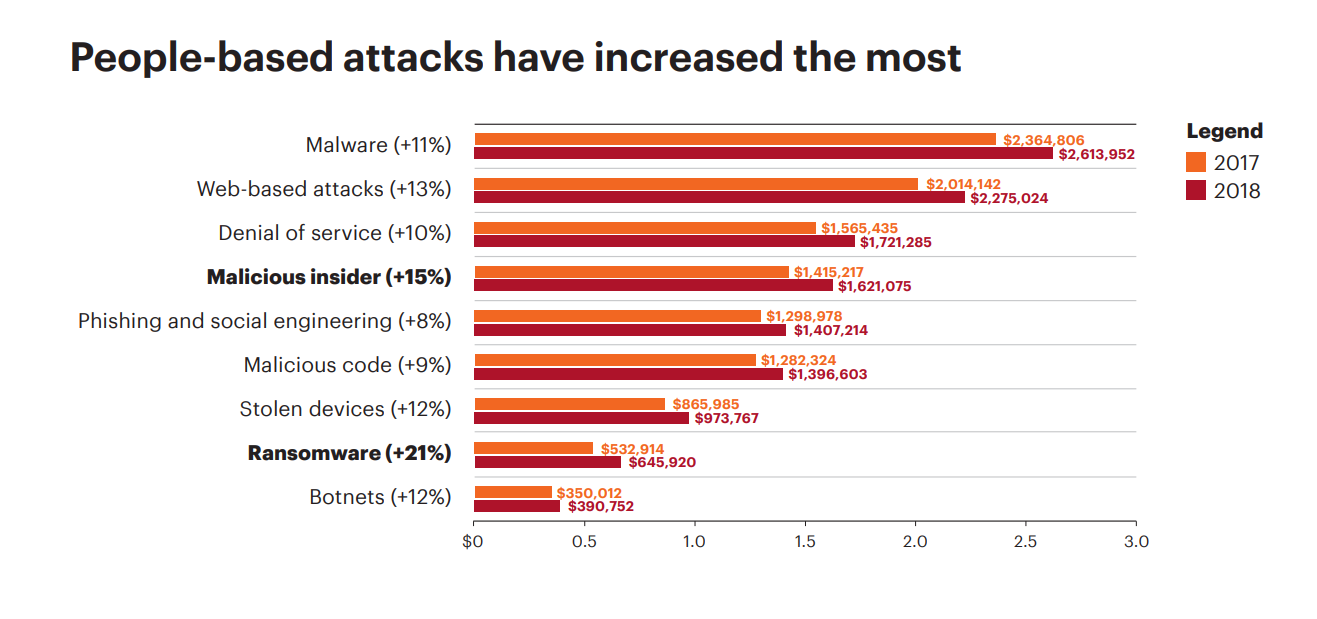 Source: Accenture
Source: Accenture
It isn’t only corporate giants that risk having their data compromised. Small to mid-sized businesses still face a threat from cybercrime even if they believe they can fly under the radar. According to the National Cyber Security Alliance, over 70 percent of small businesses were attacked, and many of them don’t bounce back.
Rewind’s own 2020 Data Protection Survey Report found that 1 in 4 ecommerce stores will lose the critical data and content that runs their store.
The increased reliance on cloud computing has created the perfect environment for cybercriminals to take advantage of unprepared companies.
7 ways to protect the data that drives your business
1. Adapt the principle of least privilege
As a company expands its online footprint, it’s common for several people in the organization to have access to the online tools required to run your business. The principle of least privilege means only the people who really need the tools to do their job should have access to them. For example, your finance team probably doesn’t need access to your code repository, and your development team probably shouldn’t have access to sensitive financial data.
Some tools offer “temporary permission” features, allowing limited time for an employee outside the core team to complete a task. This can make sure business doesn’t slow to a crawl while still offering improved data protection.
2. Use a password manager
With multiple tools come multiple passwords. The choices for office workers today can seem to be between using weak passwords that are easy to remember (“password” or “1234567” are always in the Top 10 when the results from the latest data breach are published) and strong passwords that are hard-to-remember.
Instead of trying to come up with better passwords, try implementing a password manager such as 1Password or LastPass. This makes it possible to use different strong passwords for all your online services, while you only have to remember a single master password. These managers help keep your passwords encrypted and locked away from unauthorized eyes. However, your password manager is only going to be as secure as the master password you choose for it – so test out potential passwords at a website like Security.org to see how easy it would be for a computer to hack them.
3. Embrace two-factor authentication
It has become common for online services to implement “multi-factor” authentication (MFA). In fact, if you don’t have that setup, you should. MFA tools send a unique code via SMS text or use an authenticator app on your mobile device.
If you have the option to choose between an SMS text or an authenticator app, go for the app. Many authenticator apps are not linked to only one device – giving you access to the MFA code if your phone isn’t close by. Secondly, it’s possible for hackers to steal your cell phone number and access any MFA codes being texted to you.
4. Implement encryption in the cloud
Encryption is essential to any cloud security environment. Encryption protects your data at rest, in use, and in transit to and from the cloud. Essentially, encryption translates your data into code that requires a “key” to unlock—meaning that only authorized users can access the data. The encryption code shields your data from unauthorized or malicious users, rendering it unreadable. Data in transit is most at risk, and that includes the emails you send as much as the data you save to the cloud.
5. Control access for third-party apps
It is vital to understand how much access third-party apps have to your data. Some apps request authorization to manipulate or even delete your data when they don’t need to. As a business, you must diligently read the terms and conditions to assess the level of risk you could potentially put your business in.
Reports from industry analysts like Gartner and Forrester, along with reviews from software evaluation portals like GetApp, G2 Crowd, and Capterra, can often be helpful when evaluating a vendor’s reputation and trustworthiness.
Vetting apps can be a lengthy yet necessary process. We’ve made it a bit easier for you with our simple guide to the best apps for your business.
6. Arm yourself with knowledge
Employees working from home tend to be more vulnerable to phishing attacks, malicious software, and other threats to data security. It can be hard for remote workers to stay focused with non-work-related distractions at home, making it easier to click on a suspicious link. Additionally, work from home is typically done using standard residential network equipment, which is less robust and easier to breach than the commercial-grade firewalls found at most offices.
The first step is to educate yourself and your team on how to avoid different phishing attacks. Here’s what to look for:
- Verify suspicious emails and texts with the sender by sending a new email or by picking up the phone and giving them a call.
- Ignore and delete unsolicited emails or texts from people outside the organization.
- Do not open or click suspicious documents or links in an email or text. Always verify with the sender in a different channel before taking action.
- Be suspicious; always be alert when receiving unsolicited instructions via email. If you are unsure, best to leave it.
7. Back up cloud data
When was the last time you backed up your data? If your data is ever compromised, having a backup makes recovering it a lot simpler. As easy as it may sound, there are different methods for protecting data beyond the cloud. Let’s take a look at them.
Data backup strategies
One way of protecting your data, outside of using the cloud, is to leverage the SaaS capabilities and download your data. It can be tedious and time-consuming, as well as create clutter because you will end up with many files. Keep in mind, if these files are also saved in the cloud, you are still in a compromised situation.
The second approach is to build your own backup software in-house. This is resource-intensive and lies outside the core competencies for most businesses. Even if you have the skills in-house, the opportunity costs can be prohibitive. Plus, once you’ve built a custom backup solution, you’ll still need someone to regularly perform backups and ensure everything is working as it should.
The third option is using a third-party solution for your data backup needs. Known as BaaS (Backup-as-a-Service), these companies provide automated backup and restore services that allow customers to quickly recover from accidents and/or malicious attacks with just a few clicks. This can be a great solution for smaller teams or teams that want to focus their development energy on their core product (and not running backup scripts).
Remember, always do your research, and make sure the vendor has a robust Help Centre and a history of good customer service. When it comes to lost data, you don’t want to be stuck in an endless phone tree, waiting on hold and listing to muzak – you want your problem solved quickly. Can your chosen BaaS app deliver a solution in a timely manner?
Protecting your business means protecting your data
With cybercrime threats on the rise, it’s not a matter of if data loss occurs, it’s when. Commit to constantly auditing your cloud computing data and taking the appropriate actions. Avoid future business disruptions by taking a few precautionary steps today. Back up your data, yesterday.



