The cost of a data breach in the U.S. averaged $9.44 million in 2022. And for the 12th year in a row, the U.S. holds the title for the highest cost of a data breach, $5.09 million more than the global average.
Nearly half of all data breaches happen in the cloud. This is concerning, seeing as increasing numbers of organizations are running business-critical workloads in both public and private cloud environments.
In this article, we’ll consider some of the data privacy and cloud security trends that have recently made the headlines for all the wrong reasons and what you can do to bolster your 2023 cybersecurity defenses.
Malware is morphing
Over the last year, malware variants have continued to grow in scope and sophistication. Cybercriminals are constantly adapting new techniques and strategies into their design paradigms. Every new cloud platform that emerges presents yet another potentially lucrative opportunity.
The Cybersecurity & Infrastructure Security Agency (CISA) recently published a Cybersecurity Advisory detailing the top malware in 2021. Among other findings, the Agency highlighted the adaptability and resilience of many prominent malware strains. Much of the malicious code detected has been around for years and is systematically improved on, updated, and reused. Most of 2021’s top malware has been used for more than five years, and some for more than ten years.
Unfortunately, threat actors will continue to develop and unleash new iterations of their malware, but there are ways you can reduce your risk. Here are our top recommendations:
- Develop a risk management strategy and actionable incident response plan. A risk management strategy is a structured approach to addressing security risks. It’s a cyclical process that involves risks being continually identified, assessed, managed, and monitored. An incident response plan is a set of written instructions that outline a company’s response to data breaches or leaks, cyber-attacks, and any other unwelcome security incidents.
- Regularly update your software, including operating systems, apps, and firmware.
- Always patch known exploited vulnerabilities.
- Implement network segmentation, a technique that divides a network into smaller, separate sub-networks. IT teams can compartmentalize each sub-network and deliver unique security controls and services to each. This helps prevent the spread of malware and limits attackers’ ability to move laterally across your network. One common network segmentation use case is a company’s guest Wi-Fi network: Visitors and contractors can log in with guest credentials, but they only enter a small segment or the corporate network that provides access to the internet and nothing else.
- Invest in a reliable backup solution to protect your sensitive company information from data loss, corruption, compromise, or theft. (More on this later.)
Multi-factor authentication fatigue is rife
Cybercriminals are exploiting a new phenomenon known as “multi-factor authentication (MFA) fatigue,” as seen in the recent breaches of Uber, Microsoft, and Cisco. Essentially, hackers prey on users frustrated by endless authentication approval notifications when attempting to sign in to their accounts.
In such an attack, a cybercriminal makes multiple attempts to log into a particular user’s account that’s configured with multi-factor authentication using stolen credentials. They’ll send endless sign-in approval requests to the user’s device. They may also send the targeted user emails pretending to be IT support, hoping to convince the user that the messages are legitimate requests that need their attention. Too often, the victim approves the requests out of pure frustration or believes they’ve been authorized to do so by their tech team.
While implementing two-factor authentication on your user accounts is a sound security strategy, it’s not a failsafe, and an extra layer of security is always good. For example, at Rewind, we’ve moved beyond simply allowing customers to register for multi-factor authentication (MFA) to log into the Rewind vault app.
We now also allow users to register one or more security keys compatible with the WebAuthn standard. WebAuthn Security Keys are resistant to the types of phishing schemes that other multi-factor authentication methods are susceptible to. That’s because even if you have a second factor along with a strong password, you could still fall victim to phishing or enter those credentials on a phisher’s website. With WebAuthn, users don’t have to enter passwords to authenticate themselves.
Compatible keys include either a hardware USB token such as a Yubico YubiKey, a Google Titan Key, a Feitian Security Key, or a biometric scan such as a fingerprint scanner or facial recognition scanner. Using a security key gives our customers more peace of mind, assured that their vault and account data are secure.
The effectiveness of mainstream end-user training approaches is under scrutiny
Many organizations believe that implementing security awareness training is the answer to reducing their susceptibility to cyberattacks targeting their employees. Unfortunately, many of these interventions fail to make a meaningful impact, and people continue to be the weakest link in the corporate security chain. Consider the following statistics:
- Low security awareness among employees is the top barrier for organizations looking to build better defenses against cybercrime.
- Over the last year, eight in 10 data breaches involved employee-related vulnerabilities, such as employees falling for phishing schemes and other social engineering tactics.
- 70% of users whose credentials have been compromised in breaches still use the same passwords.
- Email-based attacks led to a 28% increase in financial losses last year.
So, why are security awareness training initiatives not delivering the expected outcomes? One reason is that these programs depend heavily on periodic mock phishing email tests. IT teams keep track of user failures and use the results as indicators of the company’s overall employee-related security vulnerability.
This approach can be counterproductive, as people can start feeling resentful or even victimized. Some even succumb to “fear fatigue,” where they become demotivated to follow recommended protective behaviors. This sentiment was reported by 80% of employee respondents in a recent survey.
Humans can’t be “programmed” to behave consistently like a piece of IT equipment. Unlike machines, they don’t always follow a purely logical thought process and won’t necessarily always follow the guidance they’ve received on identifying, resisting, and reporting cyberattacks. That’s because most scams are designed to create a sense of fear or panic. Think of a hacker posing as an irate manager, impatient CEO, or an intimidating authority body like the IRS. Abrasive or threatening messages often successfully trigger powerful, knee-jerk, or emotional reactions.
Employee security awareness training will be more likely to lead to fundamental changes in individuals’ behavior if it works naturally with the human mind. People-centric rather than autocratic initiatives will have a better chance of improving the entire organization’s security posture.
Awareness of the need for reliable third-party backup for SaaS-based data is lacking
SaaS data is becoming an increasingly common cybersecurity target. A recent survey indicates that only half of victims can fully recover their data (the lowest rate of all environments.) This points to an urgent need for businesses to implement an effective SaaS data protection solution.
Although all companies participating in the abovementioned study reported they had some form of SaaS backup, only 43% said they backed up all their data. That leaves 57% of organizations at least partially unprotected.
It’s not surprising that leadership teams at only 28% of organizations are “very” confident about their ability to recover after a cloud or SaaS ransomware attack, with 69% saying they’re “somewhat” confident.
The complexity of the SaaS data recovery processes is one of the most compelling reasons for protecting SaaS data via a reliable backup solution. When asked why they’re concerned about their ability to recover, organizations are most concerned that their recovery process for SaaS data is so complex that they couldn’t quickly get up and running following a successful attack.
- 43% of respondents participating in a recent IDC survey have experienced unrecoverable data within the past 12 months.
- According to the Federal Emergency Management Agency, 40% of small and mid-sized businesses (SMBs) never reopen after a natural disaster, and an additional 25% reopen but fail within a year.
So, why aren’t more companies taking a more proactive approach to backing up their SaaS data? For some, it’s a budget and resourcing issue; for others, it’s an overreliance on SaaS platforms. Many companies still mistakenly believe that just because data is stored in the cloud, it’s safeguarded from loss. Not so. Most SaaS providers invoke the Shared Responsibility Model, limiting their liability for any form of data loss, theft, or compromise. By way of example, consider these provisions of GitHub’s terms of service:
“You understand and agree that we will not be liable to you or any third party for any loss of profits, use, goodwill, or data.”
In their terms of service, Atlassian states:
“We are not responsible for any access to or use of Your Data by third-party providers or their products or services or for the security or privacy practices of any third-party provider or its products or services. You are solely responsible for your decision to permit any third-party provider or third-party product or service to use Your Data.”
Here is what Shopify has in its terms of service:
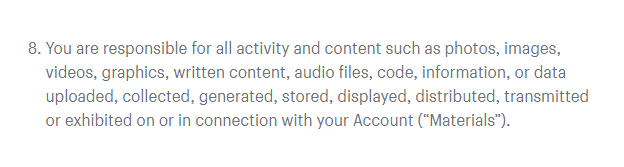
With a reliable third-party backup solution, you can take advantage of incremental backups, which essentially involve backing up only increments in data. You start with a full backup to capture every data item in your SaaS account. Subsequent backup operations only capture the changed data after the last increment. So, you back up changes more frequently, but much faster and in smaller increments. For example, if you run an ecommerce store on Shopify, you can restore product images if you accidentally delete them. If your developers want to do some exploratory coding in GitHub, but it doesn’t work out as planned, they can quickly revert to the previous iteration of the code – no rework is needed.
Make 2023 a cyber-secure year
Cyber vulnerabilities have never been rifer than they are today. The start of a new year is always a good time to look at things with fresh eyes. Investing in a reliable data backup solution to protect your critical data is a good place to start.
 James Ciesielski">
James Ciesielski">


