At Rewind, security isn’t a department. It’s what we do. With over 2 petabytes of data being secured worldwide, Rewind is continuously working to improve our security posture and better protect the data of over 100,000 customers worldwide.
Read on for an update on Rewind’s security policies, including the introduction of WebAuthn standard authentication keys like Yubikeys.
WebAuthn Security Keys: why?
Previously, Rewind allowed users to register for multi-factor authentication (MFA) using an authenticator app such as Google Authenticator or Authy Authenticator. It required a one-time passcode to be entered along with their username and password when logging into the Rewind vault app.
Now, in addition to the existing authentication options, Rewind allows users to register one or more security keys that are compatible with the WebAuthn standard. Compatible keys include either a hardware USB token such as a Yubico YubiKey, a Google Titan Key, or a Feitian Security Key, or a biometric scan such as a fingerprint scanner or facial recognition scanner.
WebAuthn Security Keys are resistant to the types of phishing schemes that other multi-factor authentication methods are susceptible to. As such, by using a security key, you can have more peace of mind assured that your vault and your account data are secure.
Using a security key with Rewind
To avoid being locked out and to ensure that you are still able to log in to your Rewind vault from any device, you can enroll multiple security keys or even a variety of multi-factor authentication methods (security key(s) and Authenticator app).
One thing to note when registering the Touch ID scanner on a MacBook is that the Touch ID security key is tied to the browser used to register the security key. However, there is no limit on the number of times that you may register Touch ID as a security key, so if you would like to use different browsers and use Touch ID as a security key, you can register it in all of the browsers that you wish to use. For example, this means you’d have a Touch ID security key for Google Chrome and a Touch ID security key for Safari.
To register a security key, go to your account settings and click on Security. The following screenshots demonstrate the registration and authentication processes for security keys:
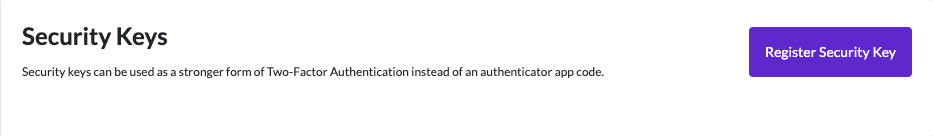
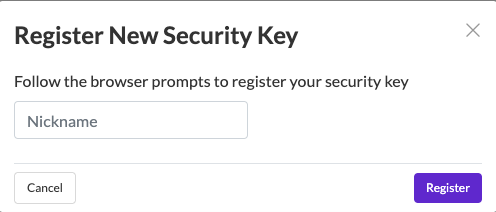
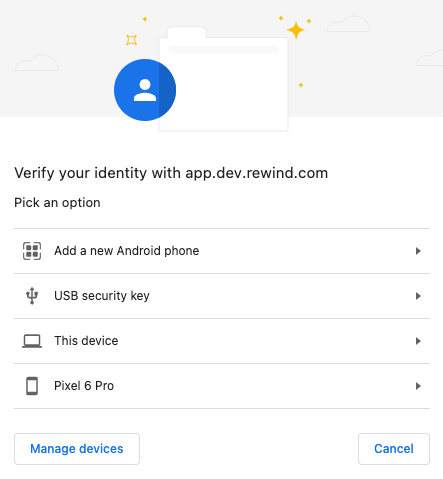
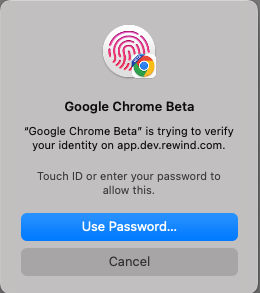
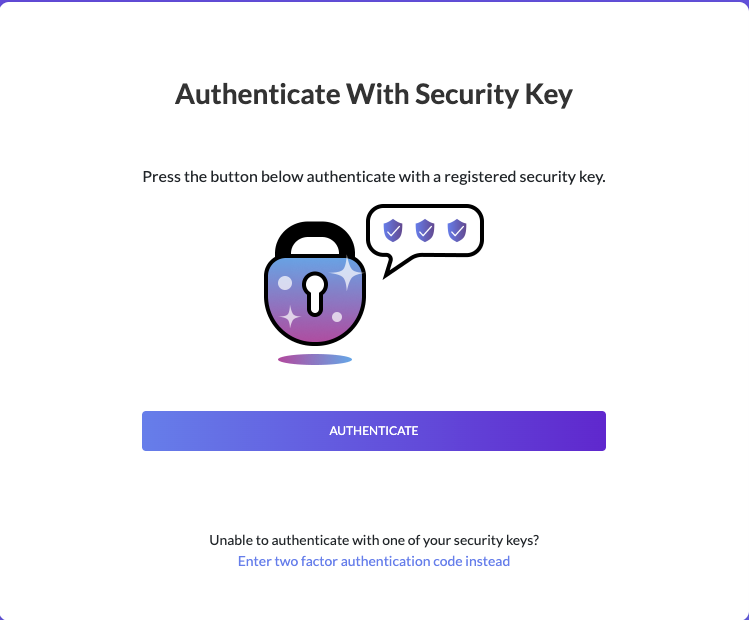
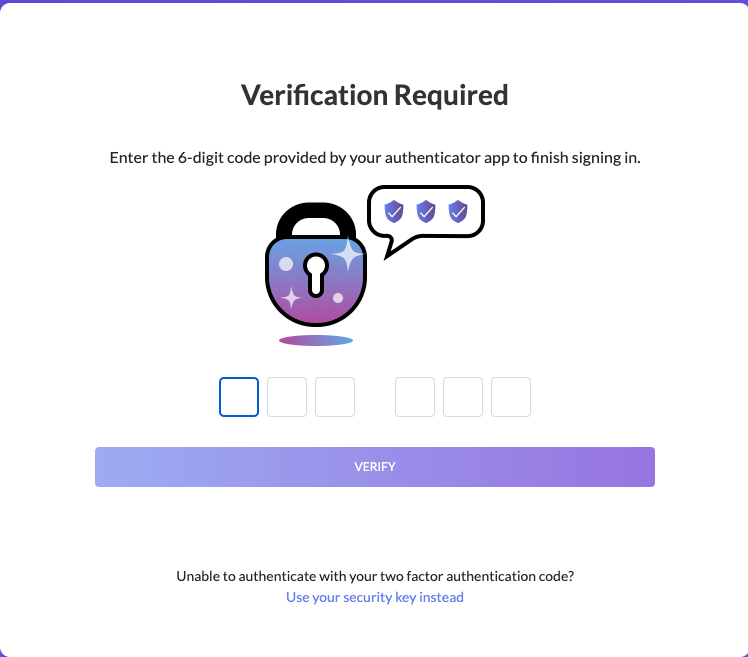
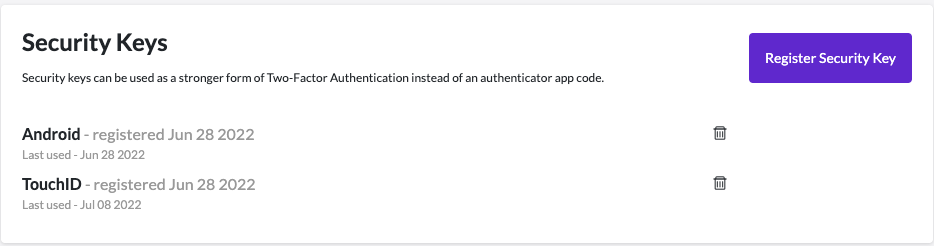
The following browsers support the WebAuthn standard and can be used to register security keys and use security keys to authenticate:
- Google Chrome for desktop version 67 and above
- Google Chrome for Android version 70 and above
- Mozilla Firefox for desktop 60 version and above
- Mozilla Firefox for Android 92 version and above
- Microsoft Edge version 18 and above
- Opera for desktop version 54 and above
- Opera for Android version 49 and above
- Safari version 13 and above
Security updates beyond authentication keys
A common component for a SaaS platform such as Rewind is an internal administration interface. This interface typically allows employees of the SaaS platform to log in and perform tasks such as running or viewing reports, performing certain customer support operations when a user is unable to self-serve, viewing system health, and more.
Rewind is no different in that we have an internal administration interface (known from here as the Rewind Admin) to help us continue to provide the level of excellent service our customers rely upon.
Unfortunately, due to the types of data available and the types of operations that an admin user can perform, these administration interfaces are becoming more and more popular a target for cybercriminals and hackers looking to either leak customer data or cause service interruptions. In fact, earlier this year, there were a number of high-profile (Okta, Microsoft, Nvidia, Samsung, and Globant) data breaches coming from malicious actors gaining access to various administration interfaces by compromising legitimate users’ credentials via social engineering attacks.
Around this time, Rewind took the following actions in order to identify gaps in the Rewind Admin:
- Performed a manual audit of what employees had access to the Rewind Admin and what role and permissions each user had.
- Performed a manual audit of what roles and permissions existed at the time.
- Identified the list of sensitive operations that can be performed within the Rewind Admin. Sensitive operations are those operations that could cause service disruptions for customers (pausing a customer’s daily backups, for example) or cause harm to Rewind – either reputationally or financially (changing the name of a customer, for example).
As a result of the above actions, the following changes were implemented to help mitigate the risks associated with a malicious user gaining access to the Rewind Admin and help to protect your data.
Reducing access in line with least privilege
From the audit of what employees had access to the Rewind Admin, it was determined that there were a number of users that had access to the Rewind Admin or that had a role with more permissions than the user should reasonably have based on the Principle of Least Privilege.
Historically, managing users and their permissions had been a manual job. As Rewind has grown, that has not scaled well and allowed for users to have access that they should not have had. As a result of this finding, we have implemented an automated process of checking users’ access and revoking access for users that no longer require it (for example, a user that required an elevated role temporarily to carry out a specific one-time task).
Following the Principle of Least Privilege is an important tenet for Rewind as it limits what a given user can view or do within the Rewind Admin. This helps to reduce what a malicious user could do or what data they could exfiltrate if they gained access to the Rewind Admin.
From the audit of the current roles and permissions, it was determined that the list of permissions – and roles by extension – were too broad. As a result, we updated the list of permissions as well as roles to be more specific. Similar to the above, this allows us to further enforce the principle of least privilege and reduce the scope of permissions that any single individual has.
Rewind Admin requires sensitive operations to follow the Two-Person Rule
That is, for any operation identified as sensitive, it now requires a second Rewind Admin user to approve the operation before it is performed. Additionally, audit logging for sensitive operations was improved to track the requester and approver, as well as information related to the request and approval, allowing us to identify potentially anomalous behavior. Along with the above changes allowing us to automate the enforcement of least privilege, implementing the Two-Person rule helps to prevent a single user from performing the most sensitive operations within the Rewind Admin (either accidentally or due to a breach by a malicious user).
At Rewind, we take security seriously, and we’re constantly looking for ways to improve all of the components of our service within the ever-changing threat landscape.
If you’ve got a mind for security and a tinfoil hat at the ready, let’s talk. Rewind is looking for dedicated security professionals to join our trust team to further improve our security posture. Join us, and help shape the future of security at a leading provider of cloud data backups.